Ruijie Community
Title: [Case Study] How to judge whether an AP is under countering? [Print this page]
Author: admin Time: 2018-4-9 11:49
Title: [Case Study] How to judge whether an AP is under countering?
Users in Building 12 in old campus cannot be associated with China UNICOM-WLAN SSID. Users associated with this SSID are often disconnected and cannot visit the Internet.
Onsite Problem Locating:
In the dormitory with poor user experience,we found that after the computer is connected to China UNICOM-WLAN SSID, the SSID signal often disappears, the ping packet loss rate is high, and the computer is often disconnected from the Internet.
We used a professional tool (Ominpeek) tocapture packets in the corridor on the second floor. A great amount ofdeauthentication (Deauth) packets were found, as shown in Figure 1.
Figure 1: Too many Deauth packets
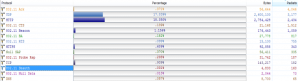
We located the AP (MAC address: 9614 4B1B 34FA) of the broadcast Deauth packet and found that it is an AP of China Unicom. After searching on the AC, we found that the AP was deployed here, covering the surrounding six rooms. But the log shows that the AP does not send any Deauth packet. Then it is confirmed that it is not this AP that sends the invalid Deauth packet.
After analysis, we suspected that there was a rogue AP. The rogue AP sent Deauth packets to the associated users in the name of China UNICOM AP, as shown in Figure 2.
Figure 2: The rogue AP broadcasting Deauthpackets in the name of China UNICOM MAC
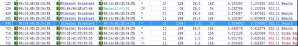
According to signal strength comparison, the signal strength of normal packet was about 26%, while that of the Deauth packet sent by the rogue AP was 100%, as shown in Figure 3.
Figure 3: Signal strength of normal packets lower than that of Deauth packets
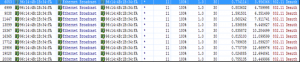
Therefore, we confirmed the existence of the rogue AP and knew that the rogueAP was close to the test place, resulting in frequent disconnection of userswithin the coverage of this rogue AP from the WLAN.
4. Locating the Rogue AP
During onsite survey, we found an AP of another carrier near the test place and the data light of this AP flashed very fast, indicating transmission of a great amount of data. This AP was suspected to be a rogue AP.
To confirm it, we powered off this AP and captured packets at the air interface on site. The result showed that the percentage of deauth packets decreased immediately from 0.239% to 0.031%, asshown in Figure 4.
Figure 4: Decreasing of deauth packets after the rogue AP is powered off
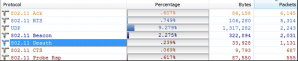
Then, the users can be associated with the AP and access the WLAN. No ping packet is lost.
After the carrier's AP is restored, the problem occurs again. Therefore, it can be confirmed that the carrier's AP is arogue AP and the AP countering function is enabled.
| Welcome to Ruijie Community (https://community.ruijienetworks.com/) |
Powered by Discuz! X3.2 |